The Limitations Of Vpns In Zero Trust Security Architecture
What is Zero Trust Security?
Zero Trust is a contemporary security framework that operates on the principle of “never trust, always verify.” It assumes that no user or device, whether inside or outside the network perimeter, should be inherently trusted. Every access request must be continuously evaluated and granted based on strict contextual checks and adherence to security policies, ensuring robust protection in today’s dynamic threat landscape.
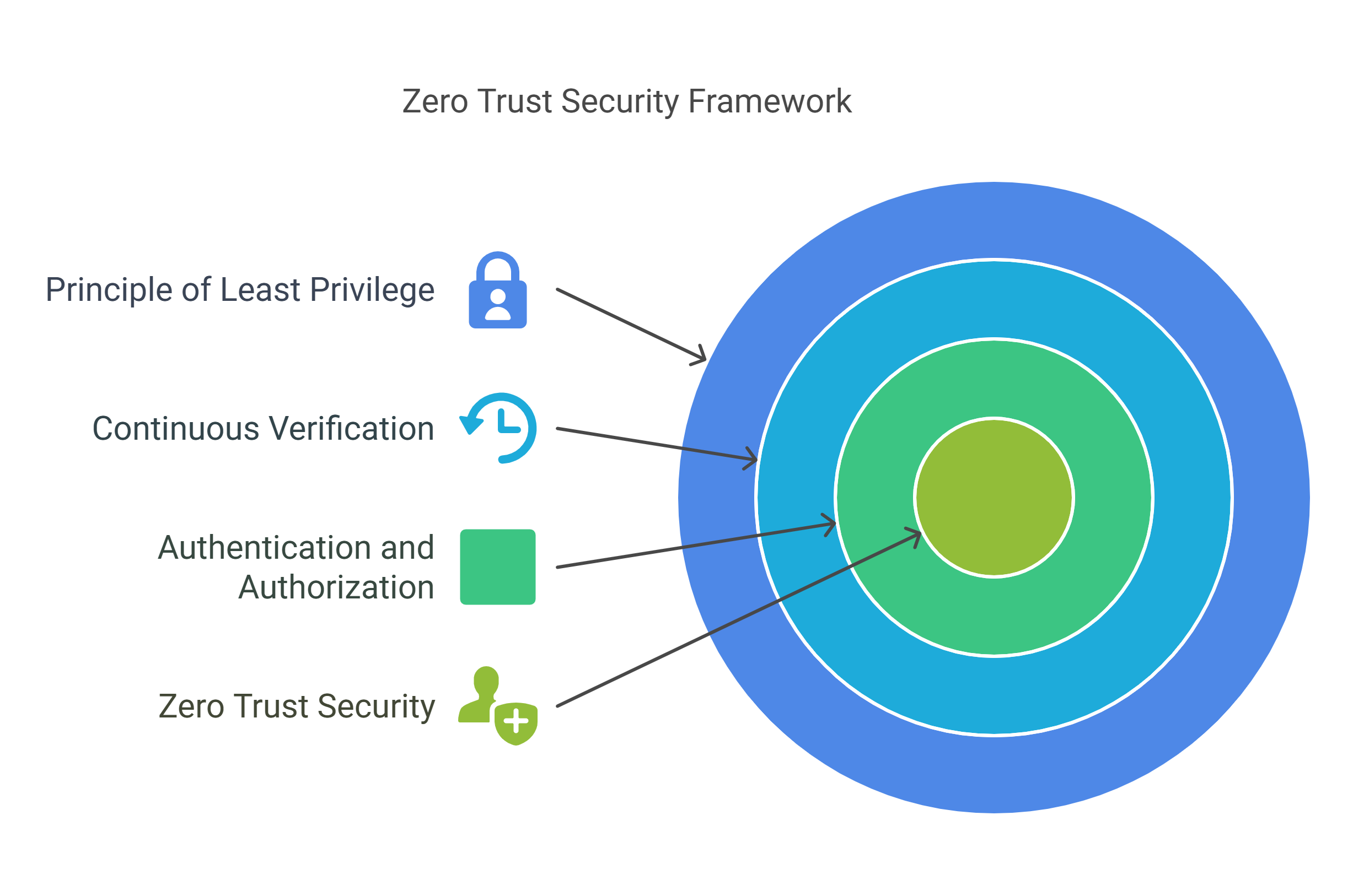
It is built on the premise that attackers could already be inside the network or might successfully breach it at any moment. As a result, it fundamentally treats all networks, including internal ones, as untrusted by default. This approach ensures that every access attempt, regardless of its origin, is subjected to rigorous scrutiny and validation. To achieve this, Zero Trust relies on three core pillars: authentication and authorization, continuous verification, and the principle of least privilege.
First, every user and device must be rigorously authenticated and authorized before gaining access to any resources. This ensures that only verified entities can interact with the network.
Second, access is not granted indefinitely. Instead, it is continuously monitored and re-evaluated based on real-time context, such as user behavior, HTTP User-Agent request header, and location. This continuous verification principle helps detect anomalous behavior and respond to potential threats dynamically.
Finally, the principle of least privilege ensures that users and devices are granted only the minimum level of access necessary to perform their tasks, reducing the risk of lateral movement by attackers within the network. Together, these principles create a robust security framework designed to adapt to modern threats.
You might be wondering, how does this relate to VPNs? Well, before drawing the connection, let’s take a moment to understand what a VPN is, what it does, and why enterprises rely on it for secure operations.
What is a VPN?
Virtual Private Networks (VPNs) have long been a foundational tool in enterprise security, particularly for enabling secure remote access. Their importance has become even more pronounced in an era of remote and hybrid work, where sensitive information is frequently shared from diverse and often unsecured locations.
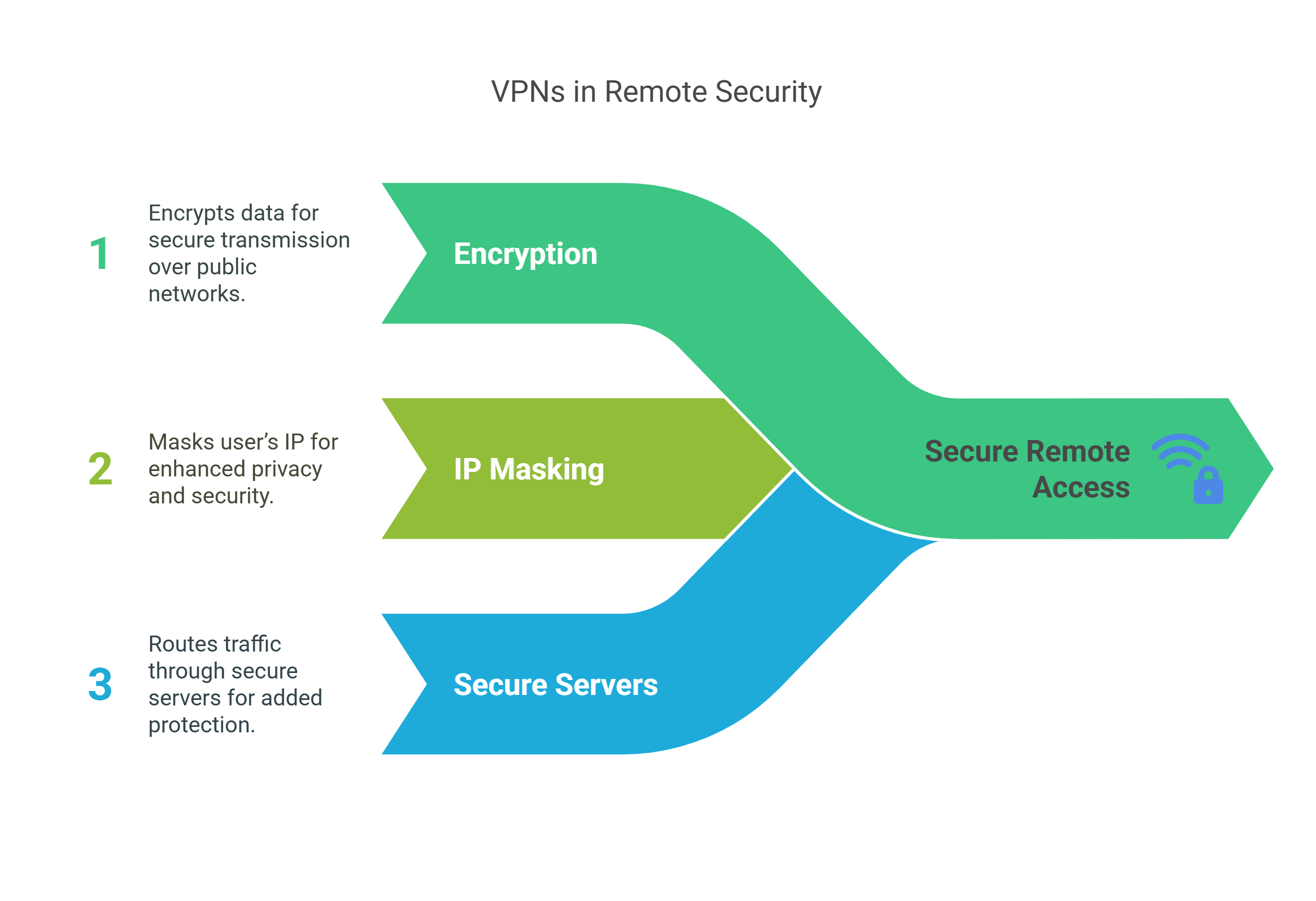
VPNs operate by extending a private network over a public one, such as the internet, through the creation of an encrypted “tunnel” for data transmission. When a user connects via a VPN, their internet traffic is encrypted and routed through a secure server.
This process not only masks the user’s IP address but also allows remote employees or branch offices to appear as if they were operating within the trusted network. This enables seamless access to internal systems and resources from virtually any location. At the same time, it safeguards sensitive data from potential eavesdropping or interception, ensuring a higher level of privacy and security for both the user and the organization.
Limitations of VPNs in a Zero Trust Framework
While VPNs secure data transmission, they fall short of Zero Trust principles in several ways. For one, VPNs struggle with granular access management. That is, they connect users to a network, not specific applications, making it difficult to enforce least privilege policies. Restricting access to individual resources often requires additional configurations, leading to over-provisioning and complexity.
Also, VPNs grant excessive implicit trust to users once they connect, placing them “inside” the network with broad access by default. This violates the Zero Trust principle of least privilege, as stolen credentials or insider threats could allow attackers to move laterally within the network unchecked. VPNs provide encrypted tunnels but lack granular access controls, leaving sensitive systems vulnerable.
Additionally, VPNs lack built-in security monitoring. They act as conduits, not firewalls, meaning any threat detection or traffic inspection requires separate security tools. Zero Trust relies on continuous monitoring and adaptive risk assessment, but VPNs offer neither, creating a “blind trust” model that contradicts Zero Trust’s “always verify” approach.
Performance and scalability present additional hurdles for VPNs. By routing all traffic through centralized gateways, VPNs introduce latency and bottlenecks, particularly in distributed or cloud-heavy environments. Scaling VPN infrastructure to support large remote workforces is both expensive and complex, often leading to sluggish connections and frustrating user experiences. In some cases, employees may even bypass the company VPN altogether to improve performance, inadvertently compromising security.
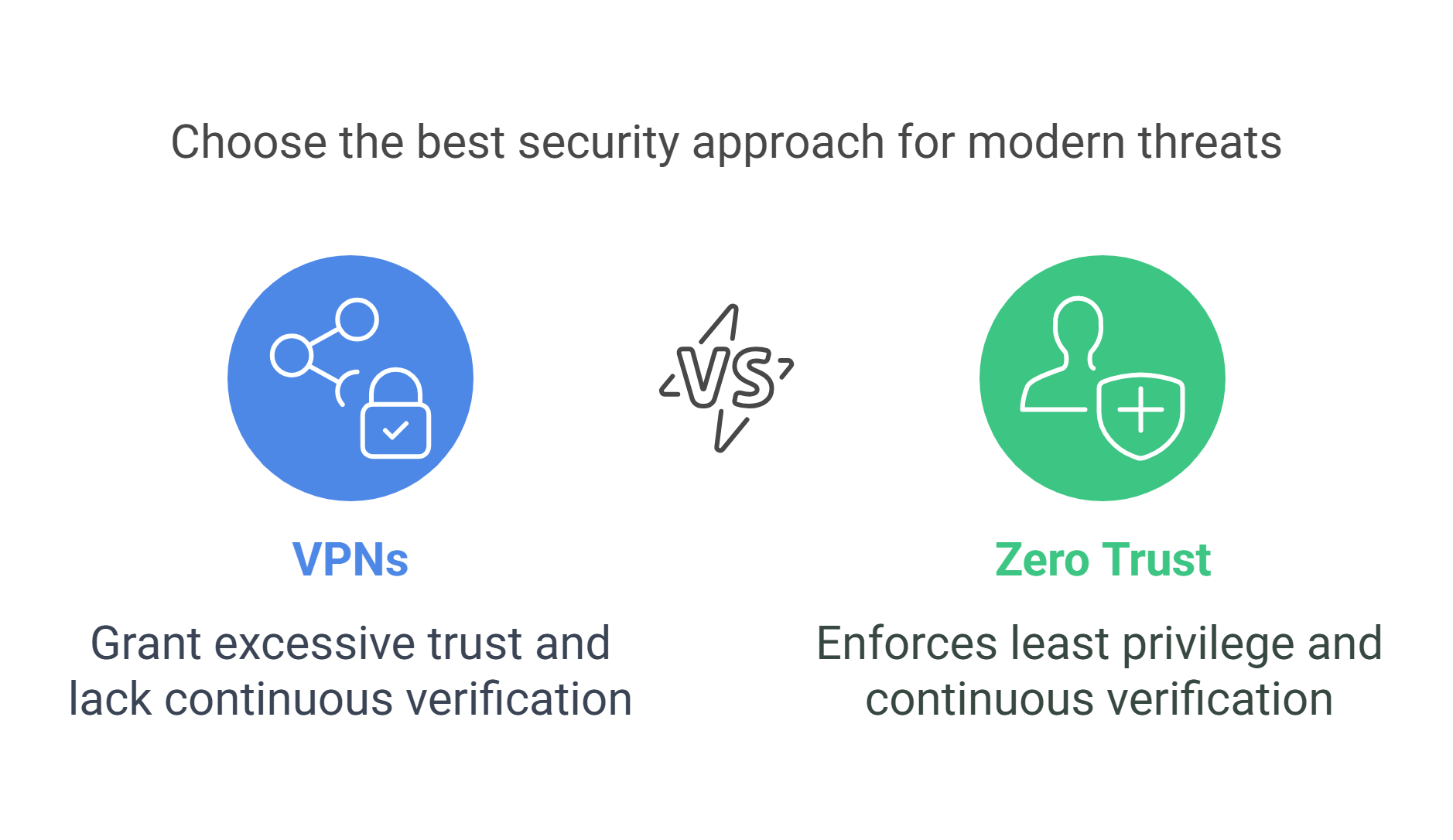
In summary, VPNs alone are fundamentally misaligned with Zero Trust. They grant excessive trust upon connection, lack continuous verification, and fail to enforce least privilege principles. Combined with performance limitations and a flat trust model, VPNs leave organizations exposed in today’s evolving threat landscape, rendering them inadequate for modern security demands.
Alternatives to VPN
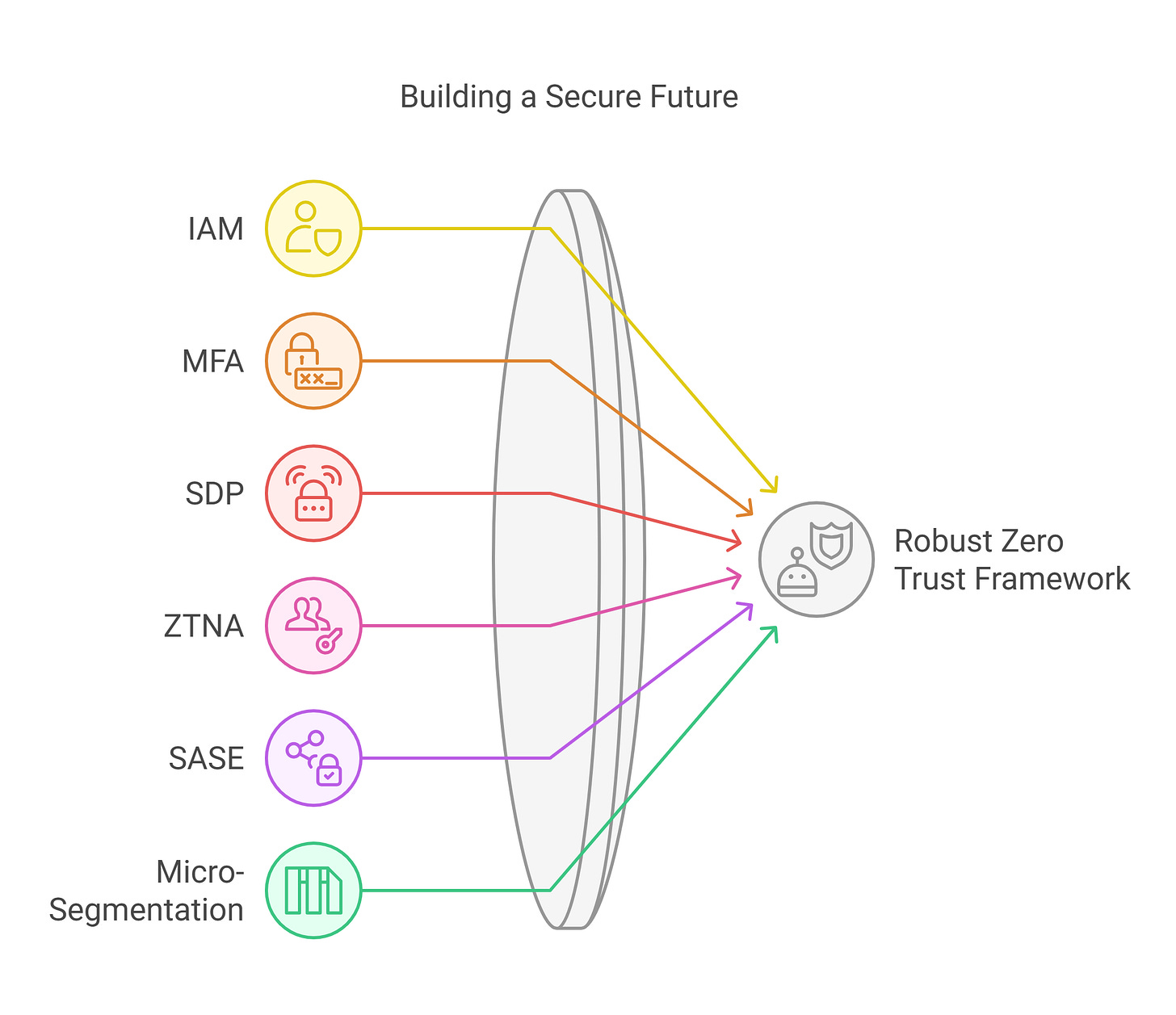
In recent years, organizations have started moving away from VPNs, adopting more robust models that prioritize Zero Trust principles to address the shortcomings of traditional approaches. At the heart of this transformation is Identity and Access Management (IAM), where identity becomes the new security perimeter, replacing the outdated reliance on network boundaries.
Implementing comprehensive IAM practices, such as role-based access control, multi-factor authentication (MFA), and identity federation, forms the foundation of a Zero Trust architecture. These tools verify user identities and enforce strict access policies before granting entry, aligning with Zero Trust’s core principle of “authenticate first.” These combined with single sign-on (SSO) and directory services, ensure that only authenticated and authorized users can access resources.
Leading tech giant Google has pioneered this approach through its BeyondCorp initiative, which eliminated VPNs by leveraging device trust and user identity to grant application access, irrespective of network location. BeyondCorp not only strengthened security but also improved user experience by enabling seamless access without the complexities of traditional VPN clients.
In addition to IAM solutions, organizations are increasingly adopting Software-Defined Perimeter (SDP) to hide internal systems until trust is established, creating a dynamic, need-to-know perimeter. Originally developed by the Defense Information Systems Agency, SDP has become a cornerstone of Zero Trust for remote access, as exemplified by Google’s BeyondCorp initiative. By granting access only after rigorously verifying identity and context, SDP provides a more secure and efficient alternative to traditional methods, minimizing exposure and enhancing control.
Alongside these advancements, the concept of Zero Trust Network Access (ZTNA) is being employed in modern architectures to replace VPNs by providing application-level access rather than broad network-level access. By verifying identity, device posture, and context before connecting users to specific resources, ZTNA ensures that everything else remains inaccessible. This least-privilege approach dramatically reduces attack surfaces and is rapidly emerging as a preferred alternative to traditional VPNs.
For organizations seeking a robust solution, Secure Access Service Edge (SASE) provides a unified, cloud-based service that integrates networking and security functions, including SD-WAN, ZTNA, and firewalls. It eliminates VPN bottlenecks by enforcing security policies closer to users, enhancing both performance and scalability.
Finally, Micro-Segmentation is another widely adopted strategy that partitions resources into small, secure zones within networks, effectively blocking attackers from moving laterally. By enforcing strict communication rules between segments, micro-segmentation minimizes the impact of breaches. When paired with identity controls, it ensures that even compromised access does not provide broad network visibility.
These technologies collectively address VPN shortcomings by enhancing identity verification, enforcing least privilege, and minimizing attack surfaces. While they share the common goal of enhancing security, each serves a unique purpose and operates at different layers of the security framework. Together, they form a robust Zero Trust framework, ensuring secure, scalable, and resilient operations in modern environments.
Moving forward, organizations should view VPNs as just one component of a broader Zero Trust strategy, used in conjunction with other controls or phased out as more adaptive solutions are implemented Embracing these principles and technologies ensures that organization’s data and systems remain secure, regardless of where access originates. The message is clear: never trust by default. Always verify, monitor, and minimize access. This is the path beyond VPNs to a more secure, agile, and future-ready security posture.
References
IBM. (n.d.). Zero Trust. Retrieved from https://www.ibm.com/think/topics/zero-trust/
Bemopro. (n.d.). From VPNs to Security Service Edge. Retrieved from https://www.bemopro.com/cybersecurity-blog/from-vpns-to-security-service-edge/
Gopher Security. (n.d.). Say goodbye to VPNs: Embrace Zero Trust Network Access (ZTNA) today. Retrieved from https://www.gopher.security/blog/say-goodbye-to-vpns-embrace-zero-trust-network-access-ztna-today
Zscaler. (n.d.). What is a software-defined perimeter? Retrieved from https://www.zscaler.com/resources/security-terms-glossary/what-is-software-defined-perimeter
Cato Networks. (n.d.). You’ll need Zero Trust, but you won’t get it with a VPN. Retrieved from https://www.catonetworks.com/blog/youll-need-zero-trust-but-you-wont-get-it-with-a-vpn/
NordLayer. (n.d.). Gartner’s take on SASE. Retrieved from https://nordlayer.com/blog/gartners-take-on-sase/